Operational Technology (OT) Cybersecurity Solutions
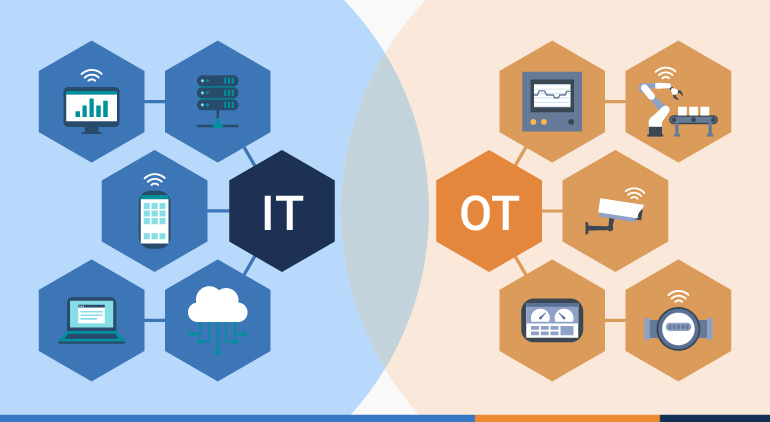
In today's digital landscape, the convergence of information technology (IT) and operational technology (OT) networks has become paramount for organizations embracing digital transformation (DX). While IT manages information within organizations, OT controls processes with direct physical impacts, making the security of these integrated environments crucial.
Traditionally kept separate, the integration of IT and OT networks offers numerous benefits such as cost reduction, productivity enhancement, and competitive advantage. However, this convergence also heightens the risk of cyber intrusions, with cybercriminals targeting IT networks to gain access to critical OT systems, leading to increased incidents of cyberattacks on essential infrastructure.
Fortinet's Comprehensive Solution for Securing IT and OT Environments
A global survey revealed that a staggering 93% of organizations experienced intrusions in their OT systems in the past year, resulting in various detrimental impacts including downtime, financial loss, and compromised safety. As a response, organizations are investing heavily in IT/OT and OT-specific security technologies to fortify their cybersecurity postures against sophisticated attacks.
Fortinet provides a comprehensive cybersecurity solution—the Fortinet Security Fabric for IT and OT—that effectively secures interconnected digital ecosystems. This solution enables full visibility across digital assets, network segmentation, access control, proactive threat detection, and streamlined security operations across Network Operations Centers (NOC) and Security Operations Centers (SOC).
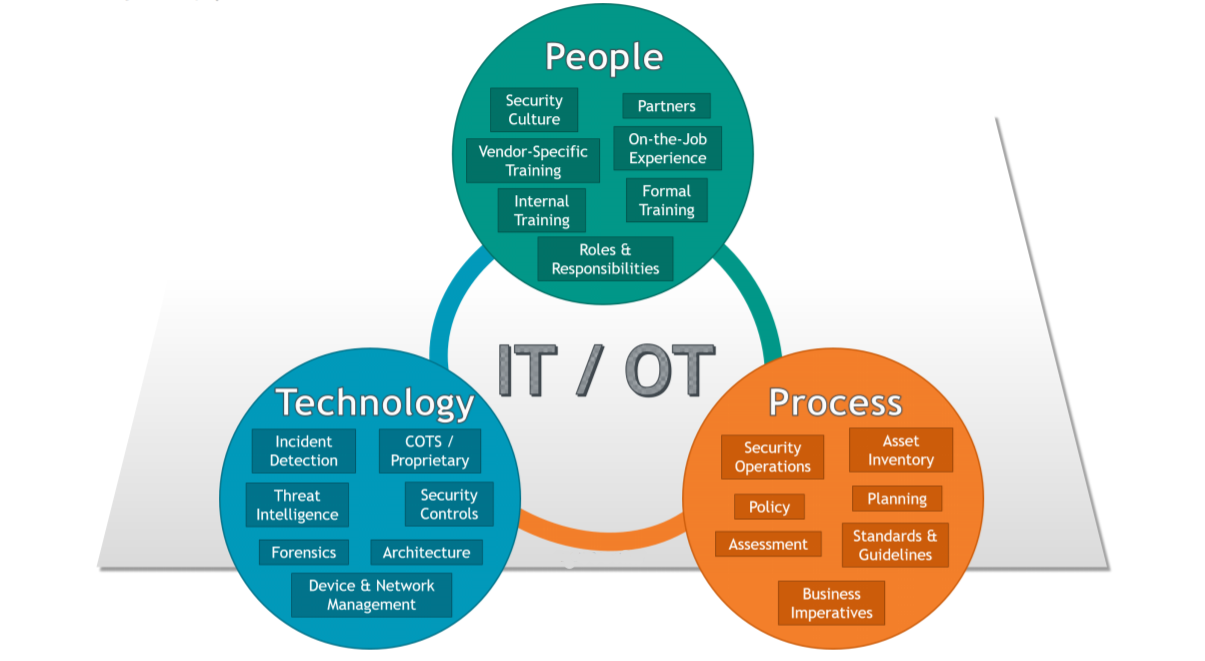
Securing OT environments requires a strategic approach, with a focus on incremental mitigation of risks and integration of security solutions. Unlike disparate point security solutions, a unified platform-based approach simplifies management, reduces complexity, and ensures consistent security across both IT and OT landscapes, minimizing technical debt and enhancing overall cybersecurity readiness.


Cyber Operational Technology (OT) Overview
The ever-increasing reliance on automation and interconnectedness within industrial control systems (ICS) has necessitated a heightened focus on OT cybersecurity.
OT security encompasses the strategies and measures deployed to protect OT systems from cyberattacks. These systems – including Supervisory Control and Data Acquisition (SCADA), Programmable Logic Controllers (PLCs), and Industrial Internet of Things (IIoT) devices – manage and monitor physical devices, processes, and events. This specialized field safeguards the critical infrastructure and processes that underpin numerous industries, including:
Why is OT Security Important?
Unlike traditional IT systems focused on data storage and processing, OT systems directly influence the physical world. A successful cyberattack on an OT system can have catastrophic consequences, leading to:
1. Disruptions in critical infrastructure operations
2. Environmental damage
3. Safety hazards for personnel and the public
4. Financial losses
Unique Challenges of OT Security
Securing OT environments presents distinct challenges compared to IT security. Here's what makes OT security so crucial: